
CAS-004 Exam Questions & Answers
Exam Code: CAS-004
Exam Name: CompTIA Advanced Security Practitioner (CASP+)
Updated: Jul 18, 2024
Q&As: 600
At Passcerty.com, we pride ourselves on the comprehensive nature of our CAS-004 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free CompTIA CAS-004 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your CompTIA CAS-004 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free CompTIA CAS-004 Dumps
Practice These Free Questions and Answers to Pass the CompTIA Advanced Security Practitioner Exam
A financial institution has several that currently employ the following controls:
1.
The severs follow a monthly patching cycle.
2.
All changes must go through a change management process.
3.
Developers and systems administrators must log into a jumpbox to access the servers hosting the data using two-factor authentication.
4.
The servers are on an isolated VLAN and cannot be directly accessed from the internal production network.
An outage recently occurred and lasted several days due to an upgrade that circumvented the approval process. Once the security team discovered an unauthorized patch was installed, they were able to resume operations within an hour. Which of the following should the security administrator recommend to reduce the time to resolution if a similar incident occurs in the future?
A. Require more than one approver for all change management requests.
B. Implement file integrity monitoring with automated alerts on the servers.
C. Disable automatic patch update capabilities on the servers
D. Enhanced audit logging on the jump servers and ship the logs to the SIEM.
An organization has been notified of a breach related to its sensitive data The point of compromise is the use of weak encryption algorithms on a web server that provides access to a legacy API The organization had previously decided to
accept the nsk of using weak algorithms due to the cost to continually develop the legacy platform.
Other system owners need to be aware of the increased likelihood of this threat.
Which of the following should be reviewed by the CERT and presented to system owners to ensure a proper nsk analysis is performed?
A. Lessons learned
B. Incident log
C. Risk register
D. Root-cause analysis
E. Gap analysis
Ann. a user, brings her laptop to an analyst after noticing it has been operating very slowly. The security analyst examines the laptop and obtains the following output: Which of the following will the analyst most likely use NEXT?
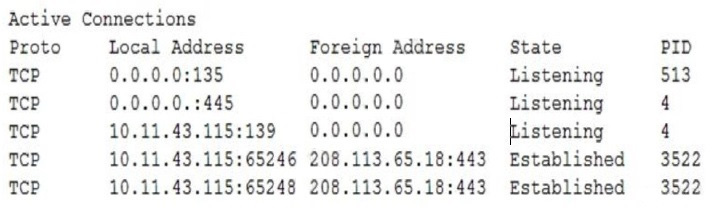
A. Process explorer
B. Vulnerability scanner
C. Antivirus
D. Network enumerator
While traveling to another state, the Chief Financial Officer (CFO) forgot to submit payroll for the company The CFO quickly gained access to the corporate network through the high-speed wireless network provided by the hotel and
completed the task. Upon returning from the business trip, the CFO was told no one received their weekly pay due to a malware attack on the system.
Which of the following is the MOST likely cause of the secunty breach?
A. The security manager did not enforce automatic VPN connection.
B. The company's server did not have endpoint security enabled.
C. The hotel did not require a wireless password to authenticate.
D. The laptop did not have the host-based firewall properly configured.
The general counsel at an organization has received written notice of upcoming litigation. The general counsel has issued a legal records hold. Which of the following actions should the organization take to comply with the request?
A. Preserve all communication matching the requested search terms
B. Block communication with the customer while litigation is ongoing
C. Require employees to be trained on legal record holds
D. Request that all users do not delete any files
Viewing Page 1 of 3 pages. Download PDF or Software version with 600 questions

