
200-201 Exam Questions & Answers
Exam Code: 200-201
Exam Name: Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)
Updated: Oct 14, 2024
Q&As: 406
At Passcerty.com, we pride ourselves on the comprehensive nature of our 200-201 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free Cisco 200-201 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your Cisco 200-201 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free Cisco 200-201 Dumps
Practice These Free Questions and Answers to Pass the CyberOps Associate Exam
What is personally identifiable information that must be safeguarded from unauthorized access?
A. date of birth
B. driver's license number
C. gender
D. zip code
How does certificate authority impact a security system?
A. It authenticates client identity when requesting SSL certificate
B. It validates domain identity of a SSL certificate
C. It authenticates domain identity when requesting SSL certificate
D. It validates client identity when communicating with the se
What is the functionality of an IDS?
A. forensic tool used to perform an in-depth analysis and debugging
B. software or device which monitors and identifies malicious network activity
C. device or software that detects and blocks suspicious files
D. endpoint protection software that prevents viruses and malware
Refer to the exhibit.
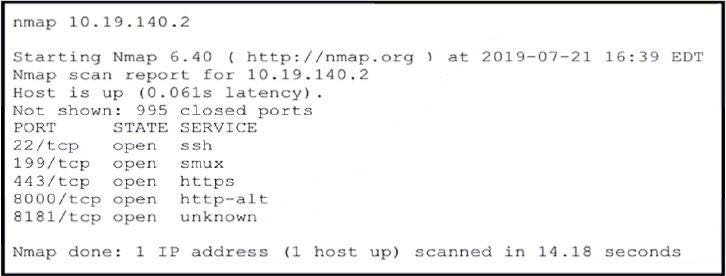
An attacker gained initial access to the company's network and ran an Nmap scan to advance with the lateral movement technique and to search the sensitive data. Which two elements can an attacker identify from the scan? (Choose two.)
A. workload and the configuration details
B. functionality and purpose of the server
C. number of users and requests that the server is handling
D. running services
E. user accounts and SID
Which piece of information is needed for attribution in an investigation?
A. attack surface and the threat posing the risk
B. attack vector and exploited vulnerability
C. asset value and an asset owner
D. threat actor and associated behavior
Viewing Page 1 of 3 pages. Download PDF or Software version with 406 questions

