
CAS-003 Exam Questions & Answers
Exam Code: CAS-003
Exam Name: CompTIA Advanced Security Practitioner (CASP+)
Updated: Jan 22, 2024
Q&As: 791
At Passcerty.com, we pride ourselves on the comprehensive nature of our CAS-003 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free CompTIA CAS-003 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your CompTIA CAS-003 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free CompTIA CAS-003 Dumps
Practice These Free Questions and Answers to Pass the CompTIA Advanced Security Practitioner Exam
A small company's Chief Executive Officer (CEO) has asked its Chief Security Officer (CSO) to improve the company's security posture quickly with regard to targeted attacks. Which of the following should the CSO conduct FIRST?
A. Survey threat feeds from services inside the same industry.
B. Purchase multiple threat feeds to ensure diversity and implement blocks for malicious traffic.
C. Conduct an internal audit against industry best practices to perform a qualitative analysis.
D. Deploy a UTM solution that receives frequent updates from a trusted industry vendor.
An external red team is brought into an organization to perform a penetration test of a new network-based application. The organization deploying the network application wants the red team to act like remote, external attackers, and instructs the team to use a black-box approach. Which of the following is the BEST methodology for the red team to follow?
A. Run a protocol analyzer to determine what traffic is flowing in and out of the server, and look for ways to alter the data stream that will result in information leakage or a system failure.
B. Send out spear-phishing emails against users who are known to have access to the network-based application, so the red team can go on-site with valid credentials and use the software.
C. Examine the application using a port scanner, then run a vulnerability scanner against open ports looking for known, exploitable weaknesses the application and related services may have.
D. Ask for more details regarding the engagement using social engineering tactics in an attempt to get the organization to disclose more information about the network application to make attacks easier.
A network engineer is upgrading the network perimeter and installing a new firewall, IDS, and external edge router. The IDS is reporting elevated UDP traffic, and the internal routers are reporting high utilization. Which of the following is the BEST solution?
A. Reconfigure the firewall to block external UDP traffic.
B. Establish a security baseline on the IDS.
C. Block echo reply traffic at the firewall.
D. Modify the edge router to not forward broadcast traffic.
Given the following output from a security tool in Kali:

A. Log reduction
B. Network enumerator
C. Fuzzer
D. SCAP scanner
A Chief information Security Officer (CISO) is developing corrective-action plans based on the following from a vulnerability scan of internal hosts:
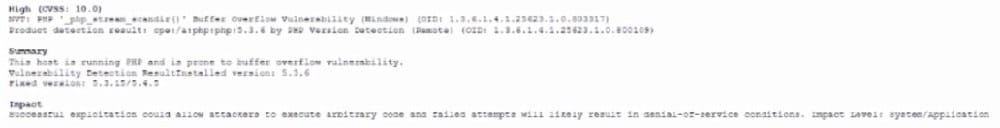
Which of the following MOST appropriate corrective action to document for this finding?
A. The product owner should perform a business impact assessment regarding the ability to implement a WAF.
B. The product owner should perform a business impact assessment regarding the ability to implement a WAF.
C. The system administrator should evaluate dependencies and perform upgrade as necessary.
D. The system administrator should evaluate dependencies and perform upgrade as necessary.
Viewing Page 1 of 3 pages. Download PDF or Software version with 791 questions

