SC-100 Exam Questions & Answers
Exam Code: SC-100
Exam Name: Microsoft Cybersecurity Architect
Updated: Apr 20, 2024
Q&As: 180
At Passcerty.com, we pride ourselves on the comprehensive nature of our SC-100 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free Microsoft SC-100 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your Microsoft SC-100 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free Microsoft SC-100 Dumps
Practice These Free Questions and Answers to Pass the Microsoft Certified: Cybersecurity Architect Expert Exam
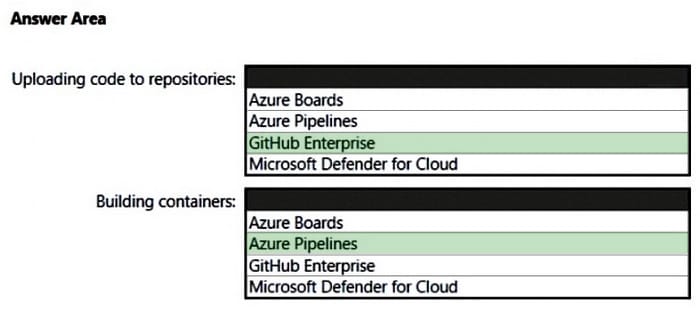
HOTSPOT
Your company has an Azure App Service plan that is used to deploy containerized web apps.
You are designing a secure DevOps strategy for deploying the web apps to the App Service plan.
You need to recommend a strategy to integrate code scanning tools into a secure software development lifecycle. The code must be scanned during the following two phases:
1.
Uploading the code to repositories
2.
Building containers
Where should you integrate code scanning for each phase? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Your company has a Microsoft 365 ES subscription.
The Chief Compliance Officer plans to enhance privacy management in the working environment.
You need to recommend a solution to enhance the privacy management. The solution must meet the following requirements:
1.
Identify unused personal data and empower users to make smart data handling decisions.
2.
Provide users with notifications and guidance when a user sends personal data in Microsoft Teams.
3.
Provide users with recommendations to mitigate privacy risks. What should you include in the recommendation?
A. communication compliance in insider risk management
B. Microsoft Viva Insights
C. Privacy Risk Management in Microsoft Priva
D. Advanced eDiscovery
Your company is moving all on-premises workloads to Azure and Microsoft 365.
You need to design a security orchestration, automation, and response (SOAR) strategy in Microsoft Sentinel that meets the following requirements:
1.
Minimizes manual intervention by security operation analysts
2.
Supports triaging alerts within Microsoft Teams channels What should you include in the strategy?
A. KQL
B. playbooks
C. data connectors
D. KQLworkbooks
Your company has devices that run either Windows 10, Windows 11, or Windows Server.
You are in the process of improving the security posture of the devices.
You plan to use security baselines from the Microsoft Security Compliance Toolkit.
What should you recommend using to compare the baselines to the current device configurations?
A. Microsoft Intune
B. Local Group Policy Object (LGPO)
C. Windows Autopilot
D. Policy Analyzer
You have a Microsoft 365 E5 subscription.
You are designing a solution to protect confidential data in Microsoft SharePoint Online sites that contain more than one million documents.
You need to recommend a solution to prevent Personally Identifiable Information (Pll) from being shared.
Which two components should you include in the recommendation? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
A. data loss prevention (DLP) policies
B. retention label policies
C. eDiscovery cases
D. sensitivity label policies
Viewing Page 1 of 3 pages. Download PDF or Software version with 180 questions