
300-915 Exam Questions & Answers
Exam Code: 300-915
Exam Name: Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)
Updated: Jul 19, 2024
Q&As: 59
At Passcerty.com, we pride ourselves on the comprehensive nature of our 300-915 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free Cisco 300-915 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your Cisco 300-915 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free Cisco 300-915 Dumps
Practice These Free Questions and Answers to Pass the Cisco Certified DevNet Professional Exam
A network is being configured for an Ethernet-connected sensor. The sensor fails to send data to the configured destination. The IP address of the sensor can be pinged from a laptop on the same subnet. When a different subnet is used, the sensor cannot be reached, but other clients on the same subnet are still accessible.
What are two reasons for the connectivity problem? (Choose two.)
A. wrong DNS server on the sensor
B. wrong subnet mask on your laptop
C. wrong default gateway on the sensor
D. wrong default gateway on your laptop
E. wrong subnet mask on the sensor
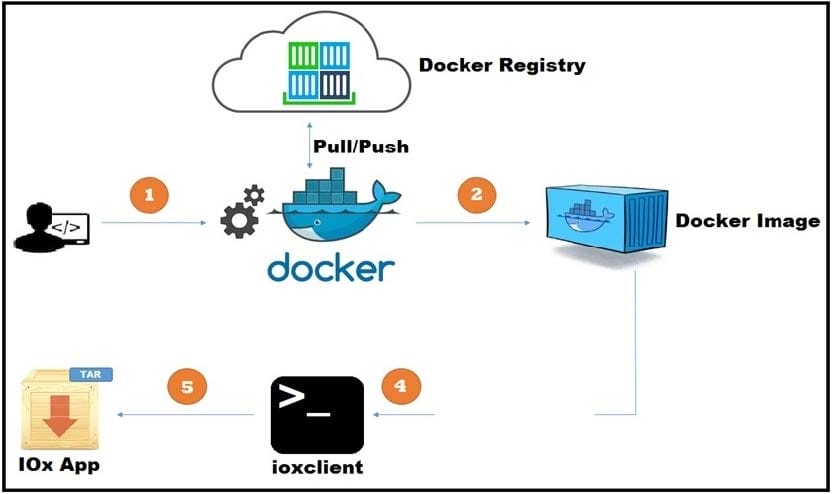
Refer to the exhibit. A new application has just been developed as a Docker container. What is the missing step for packaging the container ready for deployment in IOx?
A. Pull/push the image to the Docker registry.
B. Build the package.yaml files.
C. Build the package.cert file to sign the app.
D. Log in to device manager and load the application.
A customer is deploying sensors with Cisco IR829 routers in moving trucks to continuously monitor the health of engines using a cloud application.
Which data extraction and processing strategy is best suited in this environment?
A. No need to store data locally, upload in real time to the cloud for processing.
B. Generate local alerts and create reports at the edge, and upload to the cloud at the end of the day.
C. Use the store and forward mechanism to upload the information at the earliest to cloud.
D. Ensure that data is stored for a longer duration locally and upload to the cloud every week.
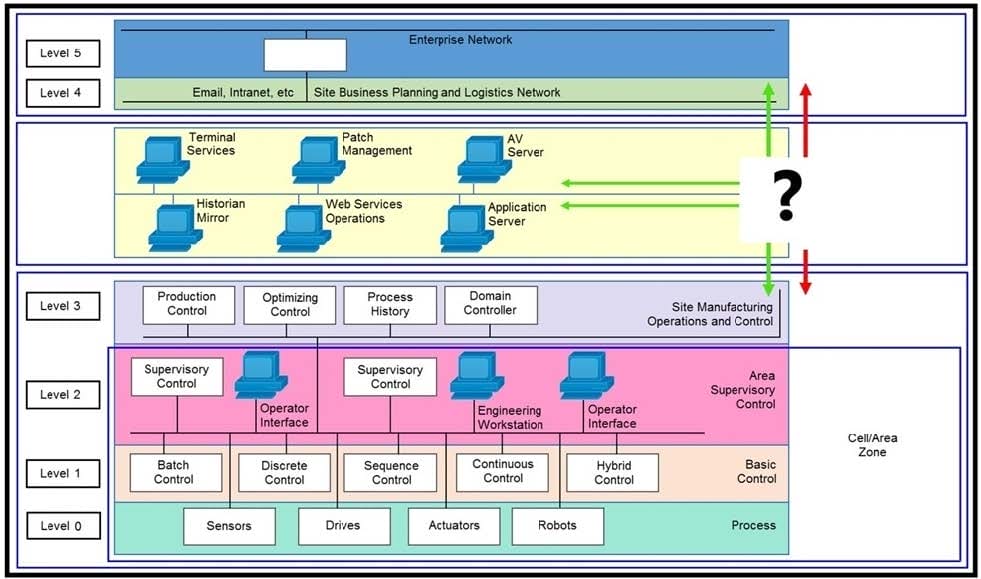
Refer to the exhibit. Which product must be positioned where the "?" is placed to connect these different network levels?
A. firewall
B. switch
C. router
D. wireless access port
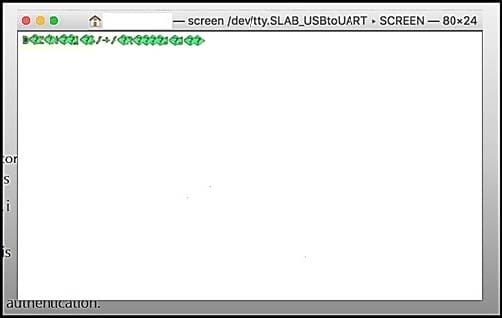
Refer to the exhibit. When a laptop is connected to a device via a serial connection, which action makes the output readable?
A. Change the baudrate in the connection settings.
B. Reboot the device in case a firmware error is the issue.
C. Change the power level of the device.
D. Change the unicode settings to UTF-8.
Viewing Page 1 of 3 pages. Download PDF or Software version with 59 questions

