
300-215 Exam Questions & Answers
Exam Code: 300-215
Exam Name: Conducting Forensic Analysis and Incident Response Using Cisco Technologies for CyberOps (CBRFIR)
Updated: Jul 24, 2024
Q&As: 59
At Passcerty.com, we pride ourselves on the comprehensive nature of our 300-215 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free Cisco 300-215 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your Cisco 300-215 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free Cisco 300-215 Dumps
Practice These Free Questions and Answers to Pass the CyberOps Professional Exam
What is the function of a disassembler?
A. aids performing static malware analysis
B. aids viewing and changing the running state
C. aids transforming symbolic language into machine code
D. aids defining breakpoints in program execution
An attacker embedded a macro within a word processing file opened by a user in an organization's legal department. The attacker used this technique to gain access to confidential financial data. Which two recommendations should a security expert make to mitigate this type of attack? (Choose two.)
A. controlled folder access
B. removable device restrictions
C. signed macro requirements
D. firewall rules creation
E. network access control
Which technique is used to evade detection from security products by executing arbitrary code in the address space of a separate live operation?
A. process injection
B. privilege escalation
C. GPO modification
D. token manipulation
An engineer received a call to assist with an ongoing DDoS attack. The Apache server is being targeted, and availability is compromised. Which step should be taken to identify the origin of the threat?
A. An engineer should check the list of usernames currently logged in by running the command $ who | cut –d’ ‘ -f1| sort | uniq
B. An engineer should check the server's processes by running commands ps -aux and sudo ps -a.
C. An engineer should check the services on the machine by running the command service -status-all.
D. An engineer should check the last hundred entries of a web server with the command sudo tail -100 /var/log/apache2/access.log.
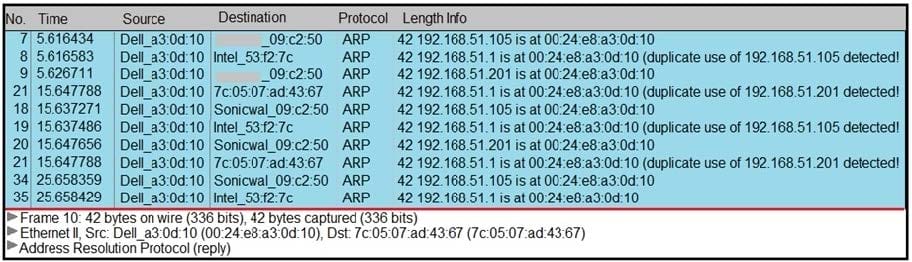
Refer to the exhibit. A security analyst notices unusual connections while monitoring traffic. What is the attack vector, and which action should be taken to prevent this type of event?
A. DNS spoofing; encrypt communication protocols
B. SYN flooding, block malicious packets
C. ARP spoofing; configure port security
D. MAC flooding; assign static entries
Viewing Page 1 of 3 pages. Download PDF or Software version with 59 questions

