
1Y0-440 Exam Questions & Answers
Exam Code: 1Y0-440
Exam Name: Architecting a Citrix Networking Solution
Updated: Apr 16, 2024
Q&As: 63
At Passcerty.com, we pride ourselves on the comprehensive nature of our 1Y0-440 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free Citrix 1Y0-440 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your Citrix 1Y0-440 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free Citrix 1Y0-440 Dumps
Practice These Free Questions and Answers to Pass the Citrix Certification Exam
Scenario: A Citrix Architect holds a design discussion with a team of Workspacelab members, and they capture the following requirements for the NetScaler design project.
1.
A pair of NetScaler MPX appliances will be deployed in the DMZ network and another pair in the internal network.
2.
High availability will be accessible between the pair of NetScaler MPX appliances in the DMZ network.
3.
Multi-factor authentication must be configured for the NetScaler Gateway virtual server.
4.
The NetScaler Gateway virtual server is integrated with the StoreFront server.
5.
Load balancing must be deployed for users from the workspacelab.com domain.
6.
The workspacelab users should be authenticated using Cert Policy and LDAP.
7.
All the client certificates must be SHA 256-signed, 2048 bits, and have UserPrincipalName as the subject.
8.
Single Sign-on must be performed between StoreFront and NetScaler Gateway.
After deployment, the architect observes that LDAP authentication is failing.
Click the Exhibit button to review the output of aaad debug and the configuration of the authentication policy.
Exhibit 1
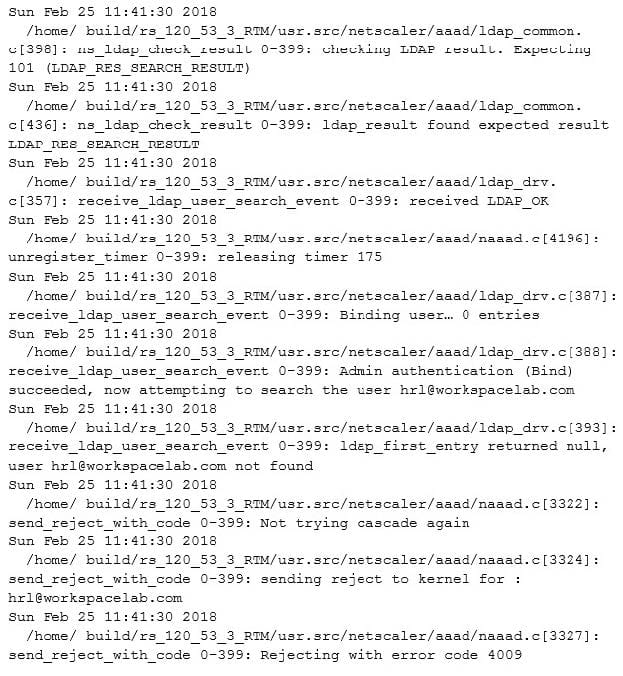
Exhibit 2
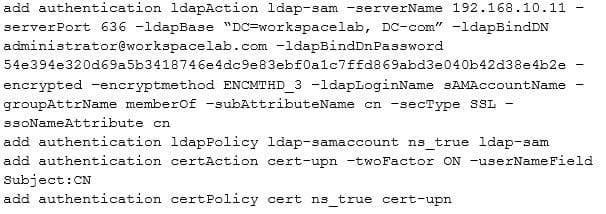
What is causing this issue?
A. UserNamefield is set as subjection
B. Password used is incorrect
C. User does NOT exist in database
D. IdapLoginName is set as sAMAccountName
Scenario: A Citrix Architect has implemented two high availability pairs of MPX 5500 and MPX 11500 devices respectively with 12.0.53.13 nc version. The NetScaler devices are set up to handle NetScaler Gateway, Load Balancing, Application Firewall, and Content Switching. The Workspacelab infrastructure is set up to be monitored with NMAS version 12.0.53.13 nc by the Workspacelab administrators. The Workspacelab team wants to implement one more pair of NetScaler MPX 7500 devices with version
12.0.53.13 nc.
The Citrix consulting team has assigned the task to implement these NetScaler devices in the infrastructure and set them up to be monitored and managed by NMAS.
The following are the requirements that were discussed during the project initiation call:
1.
NMAS should be configured to get the infrastructure information under sections such as HDX Insight, WEB Insight, and Security Insight.
2.
Configuration on the new MPX devices should be identical to MPX 11500 devices.
3.
Configuration changes after the deployment and initial setup should be optimized using NMAS.
4.
NMAS should be utilized to configure templates that can be utilized by the Workspacelab team in future deployment.
5.
As per the requirement from the Workspacelab team, NMAS should be store the audited data for only 15 days.
Which process should the architect utilize to ensure that the deployment of MPX 11500 devices are optimized and that it is correct, before deploying the devices in production?
A. Under Stylebooks; Inbuilt and composite stylebook templates should be utilized prior to deployment.
B. Under Stylebooks; Public and composite stylebook templates should be utilized prior to deployment.
C. Under Configuration Management; Configuration Audit and Advice should be used prior to deployment.
D. Under Configuration jobs; Configuration Audit and Advice should be used prior to deployment.
Scenario: A Citrix Architect needs to design a hybrid XenApp and XenApp and XenDesktop environment which will include Citrix Cloud as well as resource locations in on-premises datacenter and Microsoft Azure.
Organizational details and requirements are as follows:
1.
Active XenApp and XenDesktop Service subscription
2.
No existing NetScaler deployment
3.
About 3,000 remote users are expected to regularly access the environment
4.
Multi-factor authentication should be used for all external connections
5.
Solution must provide load balancing for backend application servers
6.
Load-balancing services must be in Location B
Click the Exhibit button to view the conceptual environment architecture.
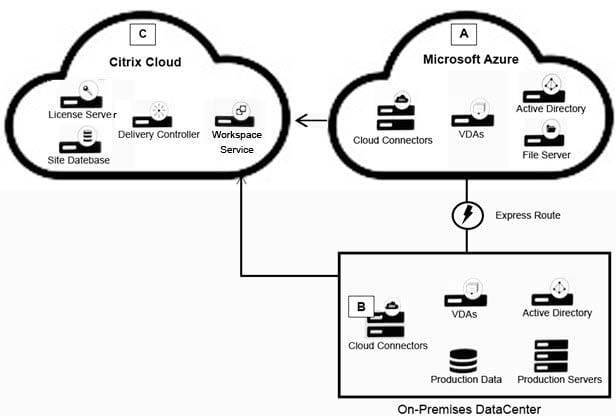
The architect should use ________ in Location A, and should use _________ in Location B. (Choose the correct option to complete the sentence.)
A. NetScaler Gateway as a Service, no NetScaler products
B. No NetScaler products, NetScaler ADC (BYO)
C. NetScaler Gateway as a Service, NetScaler ADC (BYO)
D. No NetScaler products, NetScaler ICA Proxy (cloud-licensed)
E. NetScaler Gateway as a Service, NetScaler ICA Proxy (cloud-licensed)
F. No NetScaler products; NetScaler Gateway appliance
A Citrix Architect needs to define the architect and operational processes required to implement and maintain the production environment.
In which phase of the Citrix Methodology will the architect define this?
A. Define
B. Deploy
C. Assess
D. Review
E. Manage
F. Design
Scenario: A Citrix Architect has deployed an authentication setup with a ShareFile load-balancing virtual
server. The NetScaler is configured as the Service Provider and Portalguard server is utilized as the SAML
Identity Provider. While performing the functional testing, the architect finds that after the users enter their
credentials on the logon page provided by Portalguard, they get redirected back to the Netscaler Gateway
page at uri /cgi/samlauth/ and receive the following error.
"SAML Assertion verification failed; Please contact your administrator."
The events in the /var/log/ns.log at the time of this issue are as follows:
Feb 23 20:35:21
Message 3225369 0 : "SAML : ParseAssertion:
parsed attribute NameID, value is nameid"
Feb 23 20:35:21
Message 3225370 0 : "SAML verify digest:
algorithms differ, expected SHA1 found SHA256"
Feb 23 20:35:44
Message 3225373 0 : "SAML : ParseAssertion:
parsed attribute NameID, value is named
Feb 23 20:35:44
Message 3225374 0 : "SAML verify digest:
algorithms differ, expected SHA1 found SHA256"
Feb 23 20:37:55
Message 3225378 0 : "SAML : ParseAssertion:
parsed attribute NameID, value is nameid"
Feb 23 20:37:55
Message 3225379 0 : "SAML verify digest:
algorithms differ, expected SHA1 found SHA256"
What should the architect change in the SAML action to resolve this issue?
A. Signature Algorithm to SHA 256
B. The Digest Method to SHA 256
C. The Digest Method to SHA 1
D. Signature Algorithm to SHA 1
Viewing Page 1 of 3 pages. Download PDF or Software version with 63 questions

