
PCCSA Exam Questions & Answers
Exam Code: PCCSA
Exam Name: Palo Alto Networks Certified Cybersecurity Associate
Updated: Apr 12, 2024
Q&As: 79
At Passcerty.com, we pride ourselves on the comprehensive nature of our PCCSA exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free Palo Alto Networks PCCSA Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your Palo Alto Networks PCCSA exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free Palo Alto Networks PCCSA Dumps
Practice These Free Questions and Answers to Pass the Palo Alto Certifications and Accreditations Exam
Which option lists the correct sequence of a TCP three-way handshake?
A. SYN, ACK, SYN
B. SYN, SYN+ACK, ACK
C. SYN, ACK, FIN
D. SYN, SYN+ACK, FIN
What method can be used to guarantee that a document originates from you and no one else?
A. public key encryption, encrypting the document with the private key and making the public key available to others
B. symmetric encryption, ecnrypting the document with the secret key and making a different secret key available to others
C. symmetric encryption, ecnrypting the document with the secret key and making the same secret kay available to others
D. public key encryption, encrypting the document with the private key and making the private key available to others
Palo Alto Networks App-ID uses information from which source to help identify an application in network traffic?
A. PAN-DB URL database
B. traffic behavioral analysis
C. source port in packet header
D. destination IP address in packet header
What is an effective defense against a denial-of-service attack?
A. deploy a firewall to reject suspect network packets
B. flood the DoS source with ICMP echo requests to reduce attack output
C. contact the upstream ISP and disconnect affected network interfaces
D. configure additional network interfaces for legitimate network traffic
Assume that it is your responsibility to secure the software functioning at top five layers in the exhibit.
Which cloud service model type is represented?
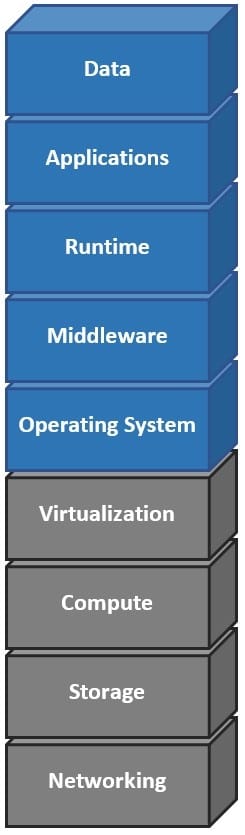
A. software as a service
B. platform as a service
C. infrastructure as a service
D. on-premises
Viewing Page 1 of 3 pages. Download PDF or Software version with 79 questions

