
NSE6_FNC-8.5 Exam Questions & Answers
Exam Code: NSE6_FNC-8.5
Exam Name: Fortinet NSE 6 - FortiNAC 8.5
Updated: Apr 20, 2024
Q&As: 30
At Passcerty.com, we pride ourselves on the comprehensive nature of our NSE6_FNC-8.5 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free Fortinet NSE6_FNC-8.5 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your Fortinet NSE6_FNC-8.5 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free Fortinet NSE6_FNC-8.5 Dumps
Practice These Free Questions and Answers to Pass the NSE 6 Network Security Specialist Exam
Which three communication methods are used by the FortiNAC to gather information from, and control, infrastructure devices? (Choose three.)
A. SNMP
B. RADIUS
C. FTP
D. CLI
E. SMTP
How should you configure MAC notification traps on a supported switch?
A. Configure them only on ports set as 802.1q trunks
B. Configure them on all ports except uplink ports
C. Configure them on all ports on the switch
D. Configure them only after you configure linkup and linkdown traps
Refer to the exhibit, and then answer the question below.
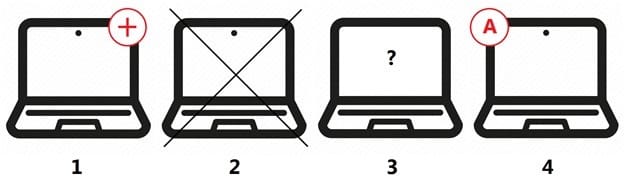
Which host is rogue?
A. 4
B. 2
C. 3
D. 1
Which three of the following are components of a security rule? (Choose three.)
A. Methods
B. User or host profile
C. Security String
D. Trigger
E. Action
What capability do logical networks provide?
A. VLAN-based inventory reporting
B. Interactive topology view diagrams
C. Application of different access values from a single access policy
D. Autopopulation of device groups based on point of connection
Viewing Page 1 of 3 pages. Download PDF or Software version with 30 questions

