
ECSAv8 Exam Questions & Answers
Exam Code: ECSAv8
Exam Name: EC-Council Certified Security Analyst (ECSA)
Updated: Apr 10, 2024
Q&As: 200
At Passcerty.com, we pride ourselves on the comprehensive nature of our ECSAv8 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free EC-COUNCIL ECSAv8 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your EC-COUNCIL ECSAv8 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free EC-COUNCIL ECSAv8 Dumps
Practice These Free Questions and Answers to Pass the ECSA Exam
Phishing is typically carried out by email spoofing or instant messaging and it often directs users to enter details at a fake website whose look and feel are almost identical to the legitimate one.
Phishing is an example of social engineering techniques used to deceive users, and exploits the poor usability of current web security technologies. Attempts to deal with the growing number of reported phishing incidents include legislation, user training, public awareness, and technical security measures.
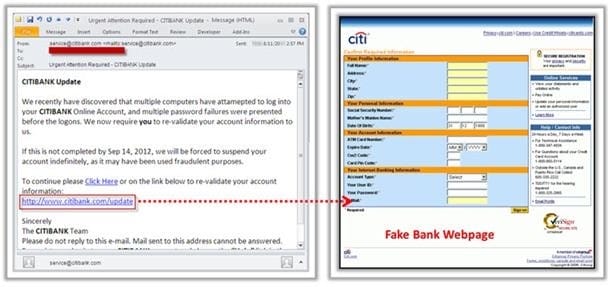
What characteristics do phishing messages often have that may make them identifiable?
A. Invalid email signatures or contact information
B. Suspiciously good grammar and capitalization
C. They trigger warning pop-ups
D. Suspicious attachments
In which of the following firewalls are the incoming or outgoing packets blocked from accessing services for which there is no proxy?
A. Circuit level firewalls
B. Packet filters firewalls
C. Stateful multilayer inspection firewalls
D. Application level firewalls
Which of the following has an offset field that specifies the length of the header and data?
A. IP Header
B. UDP Header
C. ICMP Header
D. TCP Header
The first phase of the penetration testing plan is to develop the scope of the project in consultation with the client. Pen testing test components depend on the client's operating environment, threat perception, security and compliance requirements, ROE, and budget. Various components need to be considered for testing while developing the scope of the project.
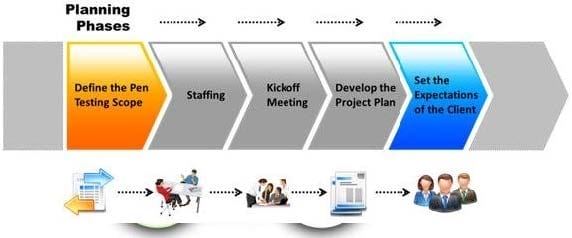
Which of the following is NOT a pen testing component to be tested?
A. System Software Security
B. Intrusion Detection
C. Outside Accomplices
D. Inside Accomplices
One of the steps in information gathering is to run searches on a company using complex keywords in Google.
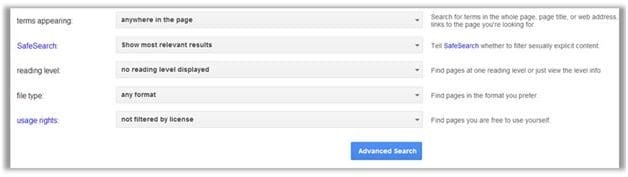
Which search keywords would you use in the Google search engine to find all the PowerPoint presentations containing information about a target company, ROCHESTON?
A. ROCHESTON fileformat:+ppt
B. ROCHESTON ppt:filestring
C. ROCHESTON filetype:ppt
D. ROCHESTON +ppt:filesearch
Viewing Page 1 of 3 pages. Download PDF or Software version with 200 questions

