
ECSAV10 Exam Questions & Answers
Exam Code: ECSAV10
Exam Name: EC-Council Certified Security Analyst (ECSA) v10 : Penetration Testing
Updated: Apr 15, 2024
Q&As: 354
At Passcerty.com, we pride ourselves on the comprehensive nature of our ECSAV10 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free EC-COUNCIL ECSAV10 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your EC-COUNCIL ECSAV10 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free EC-COUNCIL ECSAV10 Dumps
Practice These Free Questions and Answers to Pass the ECSA Exam
Karen is a Network engineer at ITSec, a reputed MNC based in Philadelphia, USA. She wants to retrieve the DNS records from the publicly available servers. She searched using Google for the providers DNS Information and found the following sites: http://www.dnsstuff.com https://dnsquery.org Through these sites she got the DNS records information as she wished. What information is contained in DNS records?
A. Information about the DNS logs.
B. Information about local MAC addresses.
C. Information such as mail server extensions, IP addresses etc.
D. Information about the database servers and its services.
Analyze the ICMP packet below and mark the correct statement.
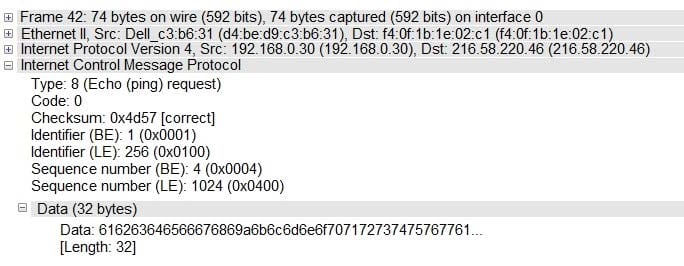
A. It is a ping packet that requires fragmentation, but the Don't Fragment flag is set
B. It is a ping request, but the destination port is unreachable
C. It is a ping response, when the destination host is unknown
D. It is a ping request, but the destination network is unreachable
Which one of the following 802.11 types uses either FHSS or DSSS for modulation?
A. 802.11b
B. 802.11a
C. 802.11n
D. 802.11-Legacy
Which of the following acts related to information security in the US establish that the management of an organization is responsible for establishing and maintaining an adequate internal control structure and procedures for financial reporting?
A. USA Patriot Act 2001
B. Sarbanes-Oxley 2002
C. Gramm-Leach-Bliley Act (GLBA)
D. California SB 1386
Paulette works for an IT security consulting company that is currently performing an audit for the firm ACE Unlimited. Paulette's duties include logging on to all the company's network equipment to ensure IOS versions are up-to-date and all the other security settings are as stringent as possible. Paulette presents the following screenshot to her boss so he can inform the clients about necessary changes need to be made. From the screenshot, what changes should the client company make? Exhibit:
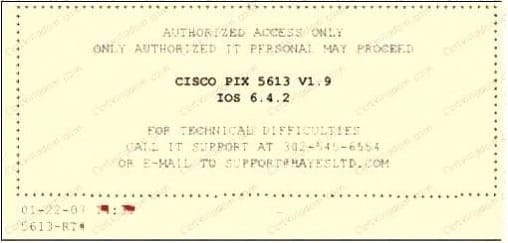
A. The banner should not state "only authorized IT personnel may proceed"
B. Remove any identifying numbers, names, or version information
C. The banner should include the Cisco tech support contact information as well
D. The banner should have more detail on the version numbers for the network equipment
Viewing Page 1 of 3 pages. Download PDF or Software version with 354 questions

