
CEH-001 Exam Questions & Answers
Exam Code: CEH-001
Exam Name: Certified Ethical Hacker (CEH)
Updated: Apr 16, 2024
Q&As: 878
At Passcerty.com, we pride ourselves on the comprehensive nature of our CEH-001 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free GAQM CEH-001 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your GAQM CEH-001 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free GAQM CEH-001 Dumps
Practice These Free Questions and Answers to Pass the GAQM certification Exam
How do you defend against DHCP Starvation attack?
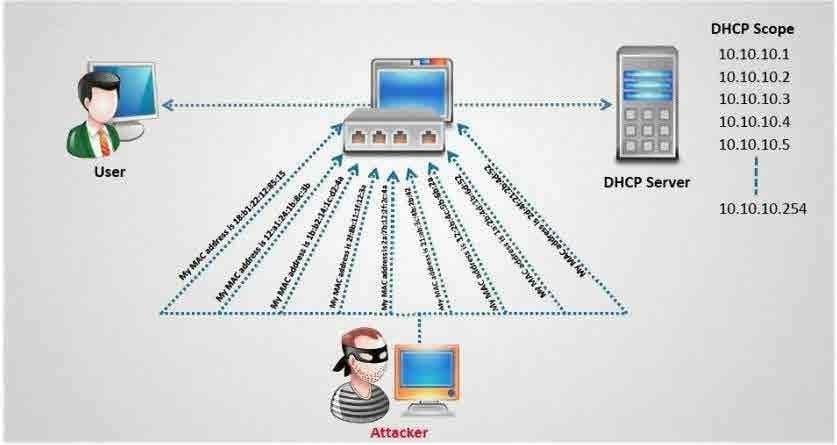
A. Enable ARP-Block on the switch
B. Enable DHCP snooping on the switch
C. Configure DHCP-BLOCK to 1 on the switch
D. Install DHCP filters on the switch to block this attack
Bob was frustrated with his competitor, Brownies Inc., and decided to launch an attack that would result in serious financial losses. He planned the attack carefully and carried out the attack at the appropriate moment.
Meanwhile, Trent, an administrator at Brownies Inc., realized that their main financial transaction server had been attacked. As a result of the attack, the server crashed and Trent needed to reboot the system, as no one was able to access the resources of the company. This process involves human interaction to fix it.
What kind of Denial of Service attack was best illustrated in the scenario above?
A. Simple DDoS attack
B. DoS attacks which involves flooding a network or system
C. DoS attacks which involves crashing a network or system
D. DoS attacks which is done accidentally or deliberately
A corporation hired an ethical hacker to test if it is possible to obtain users' login credentials using methods other than social engineering. Access to offices and to a network node is granted. Results from server scanning indicate all are adequately patched and physical access is denied, thus, administrators have access only through Remote Desktop. Which technique could be used to obtain login credentials?
A. Capture every users' traffic with Ettercap.
B. Capture LANMAN Hashes and crack them with LC6.
C. Guess passwords using Medusa or Hydra against a network service.
D. Capture administrators RDP traffic and decode it with Cain and Abel.
_________ ensures that the enforcement of organizational security policy does not rely on voluntary web application user compliance. It secures information by assigning sensitivity labels on information and comparing this to the level of security a user is operating at.
A. Mandatory Access Control
B. Authorized Access Control
C. Role-based Access Control
D. Discretionary Access Control
Which one of the following attacks will pass through a network layer intrusion detection system undetected?
A. A teardrop attack
B. A SYN flood attack
C. A DNS spoofing attack
D. A test.cgi attack
Viewing Page 1 of 3 pages. Download PDF or Software version with 878 questions

