
412-79V10 Exam Questions & Answers
Exam Code: 412-79V10
Exam Name: EC-Council Certified Security Analyst (ECSA) V10
Updated: Apr 17, 2024
Q&As: 201
At Passcerty.com, we pride ourselves on the comprehensive nature of our 412-79V10 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free EC-COUNCIL 412-79V10 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your EC-COUNCIL 412-79V10 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free EC-COUNCIL 412-79V10 Dumps
Practice These Free Questions and Answers to Pass the ECSA Exam
Which of the following policies helps secure data and protects the privacy of organizational information?
A. Special-Access Policy
B. Document retention Policy
C. Cryptography Policy
D. Personal Security Policy
A firewall protects networked computers from intentional hostile intrusion that could compromise confidentiality or result in data corruption or denial of service. It examines all traffic routed between the two networks to see if it meets certain criteria. If it does, it is routed between the networks, otherwise it is stopped.
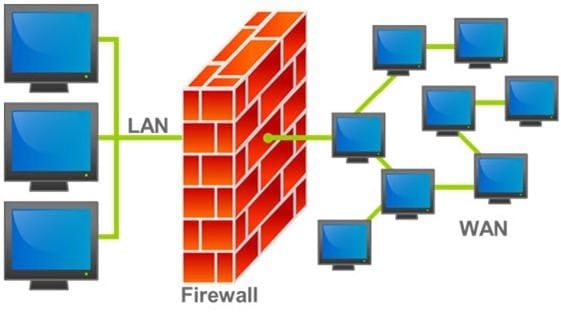
Why is an appliance-based firewall is more secure than those implemented on top of the commercial operating system (Software based)?
A. Appliance based firewalls cannot be upgraded
B. Firewalls implemented on a hardware firewall are highly scalable
C. Hardware appliances does not suffer from security vulnerabilities associated with the underlying operating system
D. Operating system firewalls are highly configured
ARP spoofing is a technique whereby an attacker sends fake ("spoofed") Address Resolution Protocol (ARP) messages onto a Local Area Network. Generally, the aim is to associate the attacker's MAC address with the IP address of another host (such as the default gateway), causing any traffic meant for that IP address to be sent to the attacker instead.
ARP spoofing attack is used as an opening for other attacks.
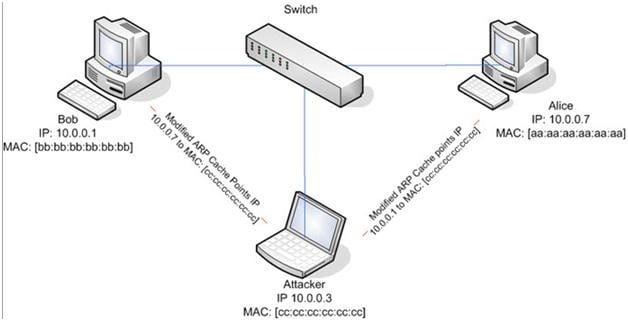
What type of attack would you launch after successfully deploying ARP spoofing?
A. Parameter Filtering
B. Social Engineering
C. Input Validation
D. Session Hijacking
Which of the following password cracking techniques is used when the attacker has some information about the password?
A. Hybrid Attack
B. Dictionary Attack
C. Syllable Attack
D. Rule-based Attack
Which one of the following tools of trade is a commercial shellcode and payload generator written in Python by Dave Aitel?
A. Microsoft Baseline Security Analyzer (MBSA)
B. CORE Impact
C. Canvas
D. Network Security Analysis Tool (NSAT)
Viewing Page 1 of 3 pages. Download PDF or Software version with 201 questions

