
312-50V9 Exam Questions & Answers
Exam Code: 312-50V9
Exam Name: Certified Ethical Hacker Exam V9
Updated: Apr 16, 2024
Q&As: 614
At Passcerty.com, we pride ourselves on the comprehensive nature of our 312-50V9 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free EC-COUNCIL 312-50V9 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your EC-COUNCIL 312-50V9 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free EC-COUNCIL 312-50V9 Dumps
Practice These Free Questions and Answers to Pass the CEH V9 Exam
Which of the following is designed to identify malicious attempts to penetrate systems?
A. Intrusion Detection System
B. Firewall
C. Proxy
D. Router
The security administrator of ABC needs to permit Internet traffic in the host 10.0.0.2 and UDP traffic in the host 10.0.0.3. Also he needs to permit all FTP traffic to the rest of the network and deny all other traffic. After he applied his ACL configuration in the router nobody can access to the ftp and the permitted hosts cannot access to the Internet. According to the next configuration what is happening in the network?
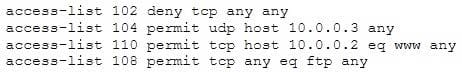
A. The ACL 110 needs to be changed to port 80
B. The ACL for FTP must be before the ACL 110
C. The first ACL is denying all TCP traffic and the other ACLs are being ignored by the router
D. The ACL 104 needs to be first because is UDP
On a Linux device, which of the following commands will start the Nessus client in the background so that the Nessus server can be configured?
A. nessus +
B. nessus *s
C. nessus and
D. nessus -d
Which of the following levels of algorithms does Public Key Infrastructure (PKI) use?
A. RSA 1024 bit strength
B. AES 1024 bit strength
C. RSA 512 bit strength
D. AES 512 bit strength
Which of the following network attacks relies on sending an abnormally large packet size that exceeds TCP/IP specifications?
A. Ping of death
B. SYN flooding
C. TCP hijacking
D. Smurf attack
Viewing Page 1 of 3 pages. Download PDF or Software version with 614 questions

