
1D0-571 Exam Questions & Answers
Exam Code: 1D0-571
Exam Name: CIW V5 Security Essentials
Updated: Apr 14, 2024
Q&As: 62
At Passcerty.com, we pride ourselves on the comprehensive nature of our 1D0-571 exam dumps, designed meticulously to encompass all key topics and nuances you might encounter during the real examination. Regular updates are a cornerstone of our service, ensuring that our dedicated users always have their hands on the most recent and relevant Q&A dumps. Behind every meticulously curated question and answer lies the hard work of our seasoned team of experts, who bring years of experience and knowledge into crafting these premium materials. And while we are invested in offering top-notch content, we also believe in empowering our community. As a token of our commitment to your success, we're delighted to offer a substantial portion of our resources for free practice. We invite you to make the most of the following content, and wish you every success in your endeavors.

Download Free CIW 1D0-571 Demo
Experience Passcerty.com exam material in PDF version.
Simply submit your e-mail address below to get started with our PDF real exam demo of your CIW 1D0-571 exam.
![]() Instant download
Instant download
![]() Latest update demo according to real exam
Latest update demo according to real exam
* Our demo shows only a few questions from your selected exam for evaluating purposes
Free CIW 1D0-571 Dumps
Practice These Free Questions and Answers to Pass the CIW Certification Exam
A new server has been placed on the network. You have been assigned to protect this server using a packet-filtering firewall. To comply with this request, you have enabled the following ruleset:
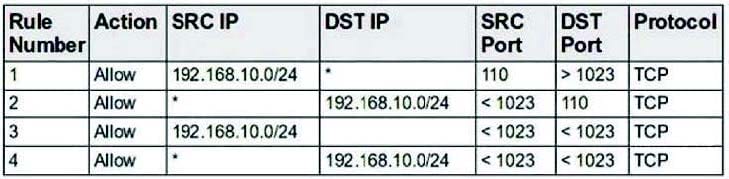
Which choice describes the next step to take now that this ruleset has been enabled?
A. From the internal network, use your Web browser to determine whether all internal users can access the Web server.
B. From the internal network, use your e-mail client to determine whether all internal users can access the e-mail server.
C. From the external network, use your Web browser to determine whether all external users can access the Web server.
D. From the external network, use your e-mail client to determine whether all external users can access the e-mail server.
Which of the following is a typical target of a trojan on a Linux system?
A. Kernel modules
B. Shared libraries
C. Boot sector files
D. System32 DLL files
A disgruntled employee has discovered that the company Web server is not protected against a particular buffer overflow vulnerability. The disgruntled employee has created an application to take advantage of this vulnerability and secretly obtain sensitive data from the Web server's hard disk. This application sends a set of packets to the Web server that causes it to present an unauthenticated terminal with root privileges. What is the name for this particular type of attack?
A. Man-in-the-middle attack
B. Trojan
C. Denial of service
D. Zero-day attack
Consider the following image of a packet capture:
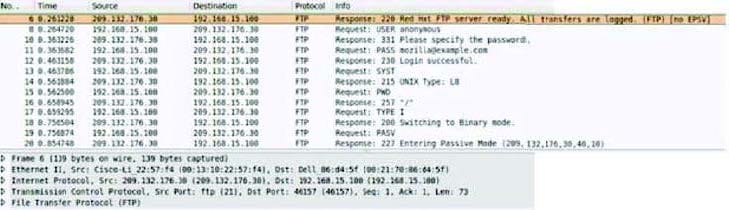
Which of the following best describes the protocol used, along with its primary benefit?
A. It is a passive FTP session, which is easier for firewalls to process.
B. It is an active FTP session, which is necessary in order to support IPv6.
C. It is an extended passive FTP session, which is necessary to support IPv6.
D. It is an active FTP session, which is supported by all FTP clients.
Which of the following is most likely to address a problem with an operating system's ability to withstand an attack that attempts to exploit a buffer overflow?
A. Firewall
B. Software update
C. Intrusion detection system
D. Network scanner
Viewing Page 1 of 3 pages. Download PDF or Software version with 62 questions

